Category: Articles
-

Google is introducing generative AI to cybersecurity
Google is among the companies competing for the emerging trend in the generative AI space. Google launched Cloud Security AI Workbench a cybersecurity suite driven by Sec-PaLM, a specialised “security” AI language model. Sec-PaLM is an outgrowth of Google’s PaLM paradigm that has been “fine-tuned for security use cases, It includes security information such as…
-

Cybersecurity: Microsoft wants more women to work in the sector
Women presently account for only 25% of the cybersecurity workforce. Microsoft Office 365 company has announced additional financing to train new cybersecurity experts, particularly women. Especially with an emphasis on some of the world’s most underrepresented regions, including South America and Asia. Argentina, Chile, Indonesia, and Spain are among the 28 nations currently covered by…
-

Google Cloud has a severe security issue
SADA is to thank for preventing a possible calamity on the Google Cloud Platform. The cybersecurity website specialists claimed to have discovered a critical vulnerability in the Google Cloud Platform. Moreover, the experts claim that it has now been patched by the tech giant. The vulnerability is known as Asset Key Theft. It allows threat…
-

Combatting Junk Mail: Keep Your Inbox Clean
An email is a fantastic tool for connecting with friends, family, and professional contacts. But regrettably, spam, commonly known as junk mail, is its awful underbelly. You must be diligent, and patient, and take certain actions to stop junk mail. The amount of spam you receive each day might not be entirely stopped or reduced…
-

Email Marketing: Best Practices for Do-Not-Reply Email Addresses
Email marketing is a cost-effective and efficient way to reach customers. However, email campaigns can be quickly dismissed if they fail to consider the customer experience. A do-not-reply email is an email that cannot be replied to. It is commonly used by email marketers to distribute information that doesn’t require a response. Although, using a…
-

Deciding on Hosting: Should You Go for Shared or WordPress
There are many different kinds of web hosting, so you must pick the one that best suits your needs. Two popular forms of hosting are shared and WordPress. Overview Sharing hosting is most popular among smaller websites and blogs because it is cost-effective and user-friendly. It is ideal for your entry point to the internet if…
-

Microsoft: Phishing email attacks targeting accountants near Tax Day
Microsoft has issued an alert on a phishing email effort that targets tax preparers and accounting companies. It uses remote access malware to gain initial access to business networks. As the USA approaches the end of its annual tax season, accountants are scrambling to collect their customers’ tax records. Because of this, it’s…
-
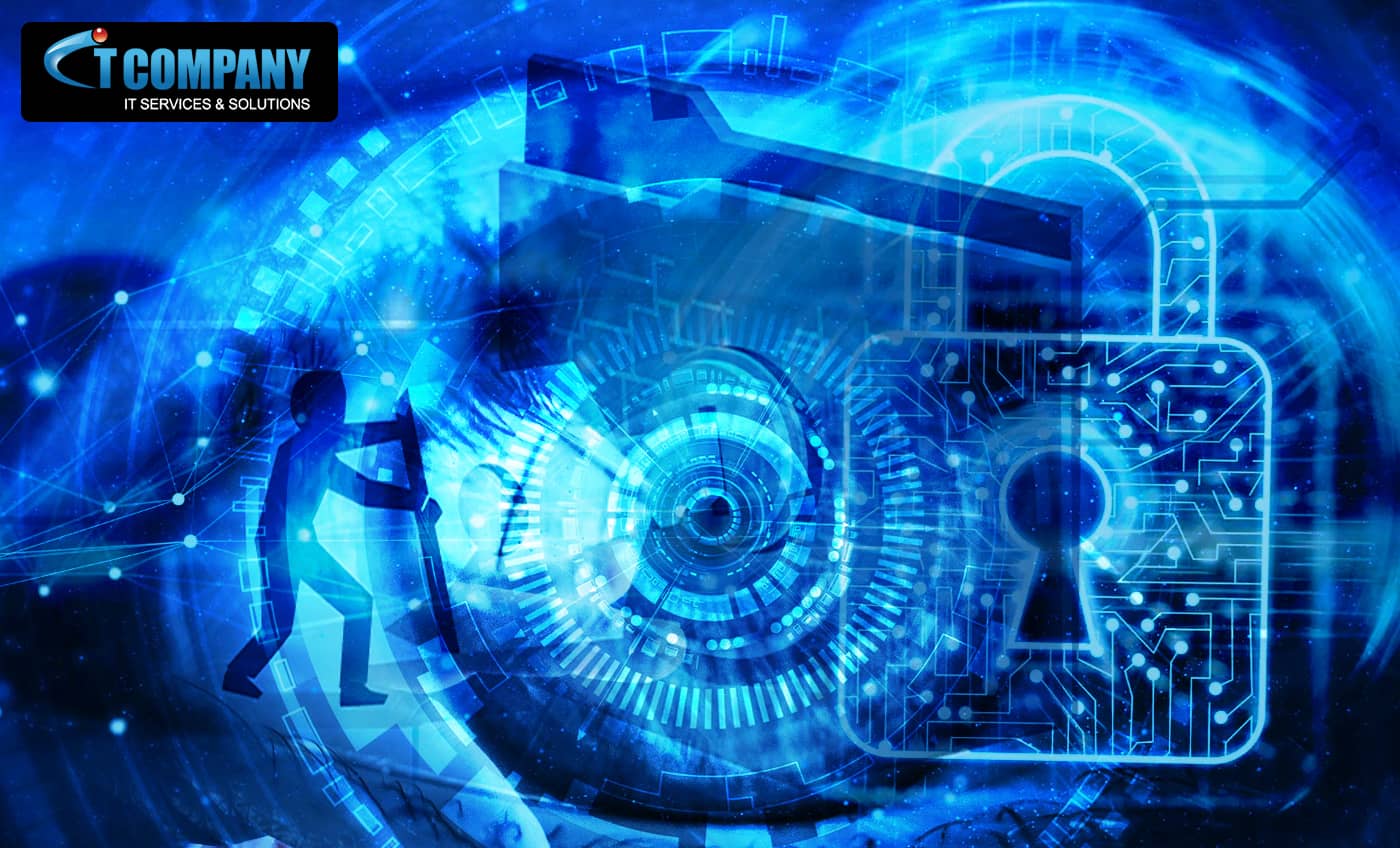
These cybersecurity tricks appear more frequently than once a year
For cybersecurity, it is advised to pay attention to the sources of information, the links, and the impersonators. Despite our awareness of these innocent practical jokes, bad actors continually try to play on our vulnerability. Common cyber-attack methods hackers use Cybercriminals utilise various techniques, including phishing assaults, malicious links, and social engineering, to…
-

Phoney Chrome upgrades distributed via Hacked websites
Unsuspecting users are exposed to malware after hackers compromise websites and insert scripts that display false Google Chrome automatic update problems. Since November 2022, the campaign has been running. However, according to the cybersecurity website expert, it picked up speed after February 2023. Moreover, it began to target people who spoke Japanese, Korean, and Spanish. Numerous websites,…
-

AI Tools Can Easily Crack Most Passwords
It’s time to reconsider your password if you believe it to be strong. A recent study from the cybersecurity website demonstrates how fast and conveniently AI Tools can decipher your password. According to statistics, 51% of frequently used passwords can be broken in about a minute. The security service website utilized PassGAN, a password generator…