
I’ll show you how to use Amazon Web Services (AWS) for disaster recovery (DR) for your self-managed Microsoft Active Directory (AD) in this blog article. In addition, as part of your overall business continuity plan, I will give an automated solution IT Company AWS Managed Cloud Hosting service to assist you in running on-demand, periodic DR testing of your AD infrastructure.
The majority of business companies utilize Microsoft AD to handle identification throughout the enterprise. Customers frequently ask how they may use AWS to establish a disaster recovery strategy. To begin with, if you use AWS Directory Service for Microsoft Active Directory, the service will manage this for you. AWS Managed takes automated daily snapshots of your directory, and in the case of a disaster, you may restore your directory from backup and resume business activities with a single click of a button.
If you run your self-managed AD on premises, I’ll show you how to use AWS as a disaster recovery solution for your AD. I’m also offering you our AWS Managed Cloud Hosting to assist you execute periodic disaster recovery exercises as part of your overall business continuity plan.
Table of Contents
ToggleOverview of the Solution
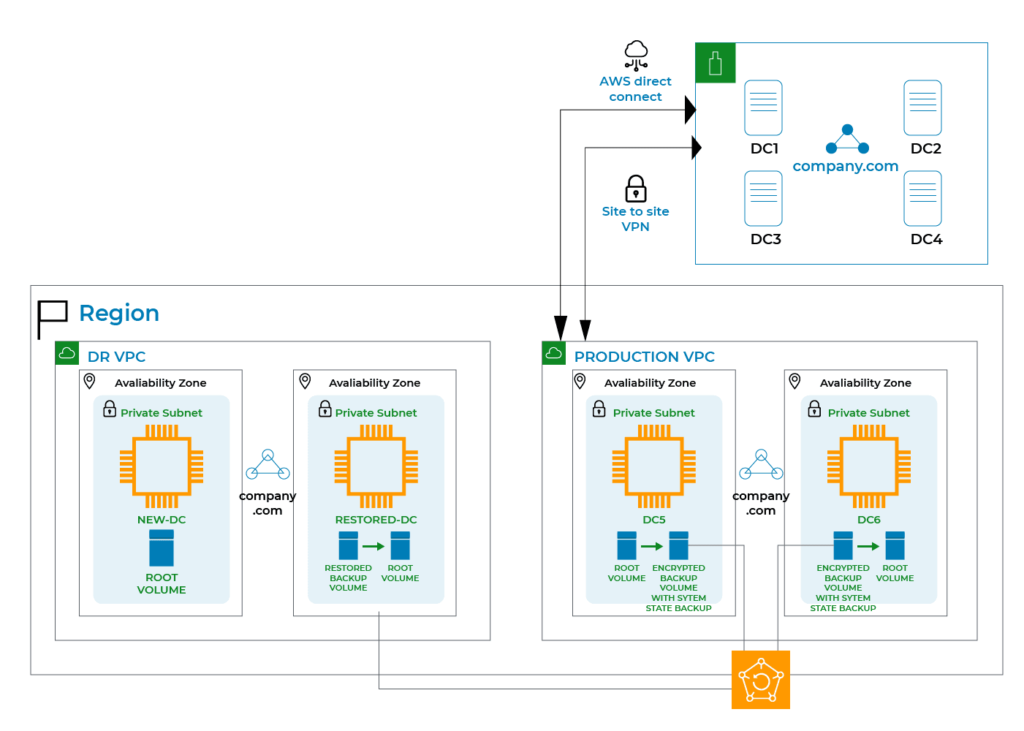
Regular backups are essential for developing an AD disaster recovery strategy. To provide comprehensive protection for your AD backup data, this recommended solution combines encrypted volumes and the AWS Backup service. You begin by backing up system state data to an encrypted backup Amazon EBS disk. As demonstrated in Figure 1, you next backup the Amazon EBS volume with AWS Backup. In the case of a disaster, you restore the Amazon EBS volume and then restore AD from the Amazon EBS volume. I give sample automation scripts to help you automate the majority of the procedure. Figure 1 shows how to extend your on-premises AD to AWS in order to use this solution for your on-premises AD.
Walkthrough
Here are the high-level steps to implement the solution:
PROTECT
The solution starts with steps to protect your AD data:
- Extend your on-premises AD to AWS by deploying at least two domain controllers in distinct AWS availability zones, as seen in Figure 1. If your self-managed AD is hosted on Amazon EC2, you may skip this step.
- Create and attach an encrypted Amazon EBS volume to each domain controller on Amazon EC2.
- Run daily system state backups to the attached secondary encrypted volumes.
- Configure AWS Backup to perform daily snapshots of the backup Amazon EBS volumes.
RESTORE
- Create a remote environment by creating a new Amazon Virtual Private Cloud (Amazon VPC) VPC, subnets, NAT Gateways, and so on.
- Launch an Amazon EC2 instance in the isolated environment.
- Restore the Amazon EBS volume containing system state backup from AWS Backup.
- Attach the backup volume to the Amazon EC2 instance.
- Restore the system state backup from the backup volume.
- Carry out the measures for AD Forest rehabilitation.
Prerequisites
The instructions in this post presume that you know how to establish Amazon EC2 instances and how to connect in to the instances using Remote Desktop Protocol (RDP). These instructions presume that you have extended your on-premises AD to Amazon EC2 if you are operating AD on premises. Please see this blog.
Configure AD protection
In this part, you will configure two tiers of daily backup of your AD data. First, set up an automatic daily system state backup to Amazon EBS. A domain controller’s system state backup includes AD data.
Then, using AWS Backup, you will set up an automated daily backup of the Amazon EBS volume holding the system state backup.
STEP 1: Set up daily AD backups to Amazon EBS.
Complete the steps below to set up an automatic daily system state backup of AD to Amazon EBS.
1. Make an encrypted Amazon EBS volume.
2. Connect the Amazon EBS volume to one of the Amazon EC2 domain controllers.
3. Allow Windows access to the Amazon EBS volume.
4. Set up an automatic system state backup to the Amazon EBS volume by following the procedures in this manual. You may also use the script below to accomplish this. This script generates a scheduled process that performs a system state backup to the secondary Amazon EBS volume on a daily basis at 1:00 a.m. In my case, the backup Amazon EBS volume’s drive letter is “d:”.
Code:
#Install-WindowsFeature Windows-Server-Backup Install-WindowsFeature Windows-Server-Backup
# Make a new folder to hold the backup script.
C:System_State_Backup_Script -ItemType Directory -Force New-Item
# Write the backup script and store it to the folder @’ # Configure Backup Options
New $Policy-WBPolicy
New $BackupLocation-WBBackupTarget -VolumePath D: $Policy Add-WBSystemState
-Policy -WBBackupTarget Set-WBVssBackupOptions $Policy -Target $BackupLocation -VssCopyBackup $Policy
“Start System State Backup job” writes out.
Attempt Start-WBBackup -Policy $Policy -Async -Force Detect [System.Exception] “unable to start system state backup” write-output
# Verify that the backup job is still executing.
Set-Content -Path “C:System_State_Backup_ScriptSystemStateBackup.ps1” Get-WBJob ‘@ | Set-Content -Path “C:System_State_Backup_ScriptSystemStateBackup.ps1”
# Make a Scheduled Task to execute the backup script on a regular basis.
New-ScheduledTaskAction $taskAction -Execute “powershell.exe” -Argument “C:\System_State_Backup_Script\SystemStateBackup.ps1”
$taskTrigger = New-ScheduledTaskTrigger -Everyday -At1am
“SystemStateBackup” is the name of the task.
$description = “Every day at 1am, performs a system state backup.”
STEP 2: Use AWS Backup to safeguard the Amazon EBS volume
Set up AWS Backup to take frequent snapshots of the volume holding AD data that you setup in step 1 to secure it. This is an important step to guarantee that you have several copies of the backup disk. AWS Backup is a fully managed solution that simplifies the centralization and automation of data protection across AWS services, in the cloud, and on premises. To schedule AWS Backup for the Amazon EBS volume containing AD data, do the following steps:
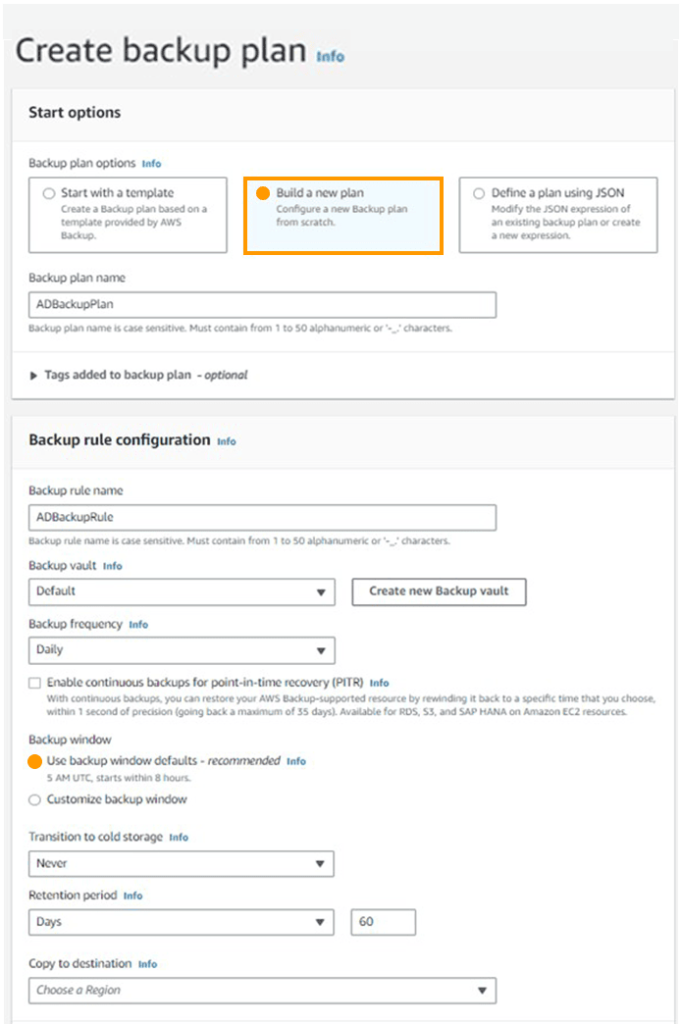
1. Select Backup Plans from the AWS Backup interface.
2. As seen in Figure 2, pick Create Backup Plan and then Build a New Plan.
3. Enter a name for both the Backup plan name and the Backup rule name. 4. Select Daily for backup frequency and a number for retention.It is important to note that the figure you choose should not be greater than the tombstone lifetime. An earlier backup than the tombstone lifespan is invalid and cannot be utilized to restore AD. For further information, consult the Microsoft documentation. Also, when determining the backup time, keep in mind the daily system state backup time you established in step 1. You want AWS Backup to finish the system state backup before beginning the snapshot backup of the Amazon EBS volume.
5. If you want to produce a copy, pick your chosen AWS Region for Copy to Destination and create a Backup Plan.
Running DR drills for your assistant director
You should conduct frequent DR drills as part of your AD DR plan. This validates the backups and guarantees that you are prepared in the case of a calamity. This section explains how to restore AD from backup.
STEP 1: Restore Amazon EBS including AD data from AWS Backup
In this step, you will restore the Amazon EBS snapshot that contains the system state backup from AWS Backup. AWS Backup produces a new Amazon EBS volume that you may attach to your Amazon EC2 instance when you restore an Amazon EBS snapshot. You will utilize the recovered volume to retrieve AD for your DR drill.
To recover the Amazon EBS volume containing the system state data from AWS Backup, perform the following steps:
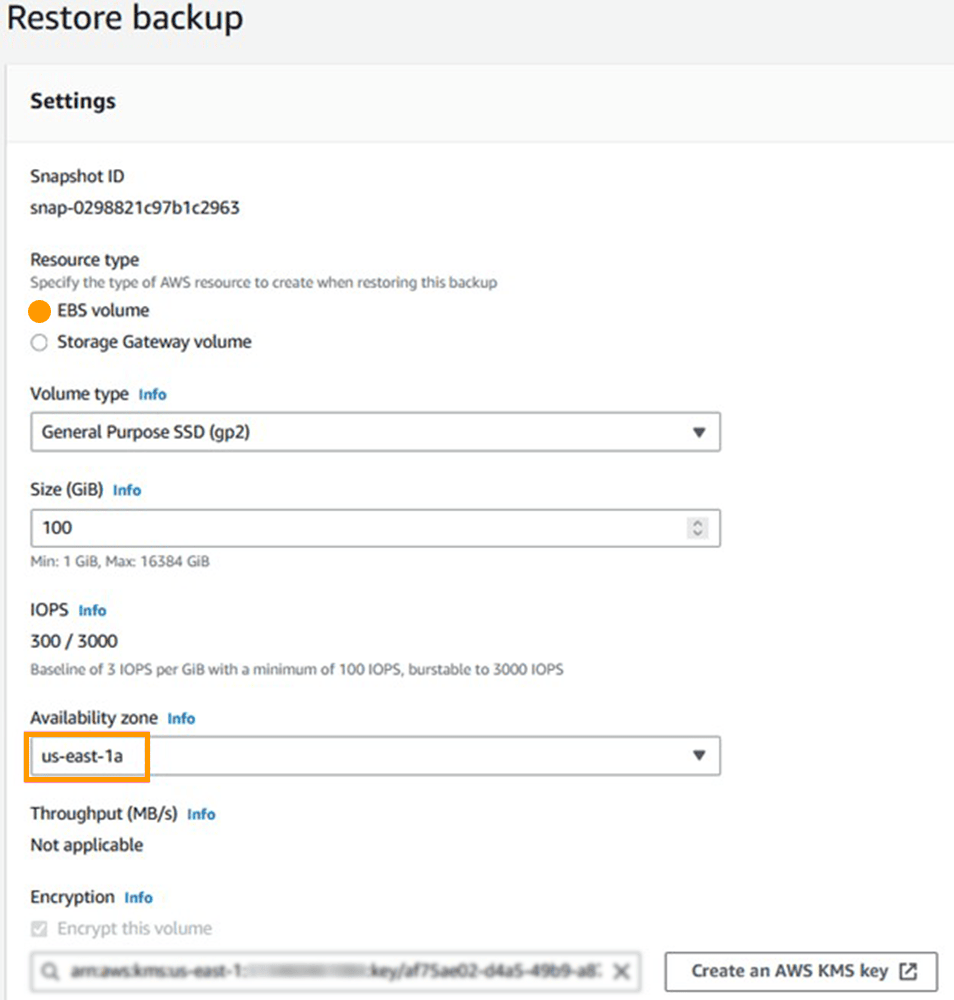
1. Select Protected Resources in the navigation pane of the AWS Backup interface.
2. Select the volume ID, a Recovery point ID, and Restore.
3. As illustrated in Figure 3, on the Restore backup screen, pick an availability zone and click Restore backup. Make a note of the availability zone you choose, since you will need it in the following step. In my case, I choose to restore the volume to us-east-1a.
STEP 2: Restore the AD forest at a remote location
You are now ready to recover AD after restoring the Amazon EBS volume from AWS Backup. During a DR exercise, restore AD to an isolated environment to avoid affecting your production environment. Create a new VPC, run a new Amazon EC2 instance into the VPC, attach the restored Amazon EBS volume to the Amazon EC2 instance, then execute system state recovery from the associated volume to the instance to restore AD in isolation. To finish the AD recovery process, you will need to undertake a series of AD forest recovery operations. More information is available in the Microsoft documentation. This approach might be time consuming, especially if you intend to conduct frequent DR exercises for your AD environment.
To make things easier, I’ve created an AWS CloudFormation template that you can deploy on-demand to create the isolated environment and perform the system state recovery automatically. I also include a second script that conducts the aforementioned forest recovery measures.
To deploy the AWS CloudFormation template and execute the AD forest recovery script, follow these steps:
1. Install the CloudFormation template.
2. Navigate to the AWS CloudFormation console.
3. Choose With new resources (standard) for the Create Stack option.
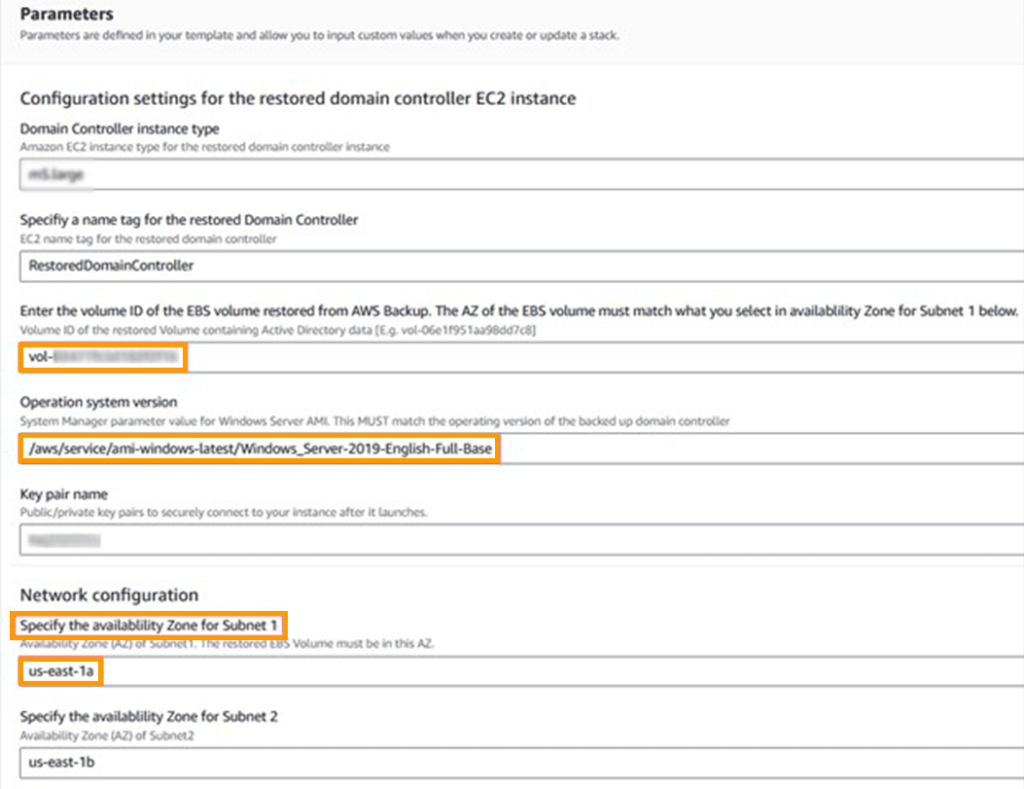
4. Choose Upload a template file as the Template source. Choose File, then the template you downloaded in step 1 and Next. 5. The template populates the majority of the data on the Specify stack details page. Enter the Volume ID of the Amazon EBS volume you restored from AWS Backup. When defining an availability zone for subnet 1, ensure that it corresponds to the availability of the Amazon EBS volume you mentioned in the previous section, as illustrated in Fig 4. This guarantees that the domain controller instance can mount the recovered EBS disk. Complete the remaining fields and then click Next.
You must also choose the same operating system and AWS generation Amazon EC2 instance type as the domain controller used for the system state backup in step 1. I tried and suggest AWS Nitro System instances.
- On the Configure stack settings screen, click Next.
- On the Review stack name screen, check the box next to I understand that AWS CloudFormation may generate IAM resources with custom names and click Submit.
- Once the AWS CloudFormation stack has been created, access the AWS Systems Manager Automation console and wait for the automation to finish the System State restoration procedure.
- Modify the security group of the bastion Amazon EC2 instance to enable your IP address and RDP logon. Log in to the recovered domain controller instance via RDP from the bastion instance and download the AD forest recovery PowerShell script.
The script accomplishes the following:
- Adds an Amazon EC2 instance metadata service route.
- Executes a SYSVOL authoritative restore. Refer to the Microsoft manual for further details.
- Takes up the FSMO functions.
- Executes the ntdsutil.exe command-line tool to perform AD metadata cleanup on all domain controllers in the AD database except the one where the command is being executed.
- Deletes all DNS entries containing any of the previously removed domain controllers.
- Increases the accessible RID pool’s value by 100,000.
- Sets up the Windows Time service.
- Run the script in PowerShell as administrator. In my case, I saved the script as RecoverAD.ps1 after downloading it to “c:scripts.” I used the following command to execute the script: C:\scripts\RecoverAD.ps1
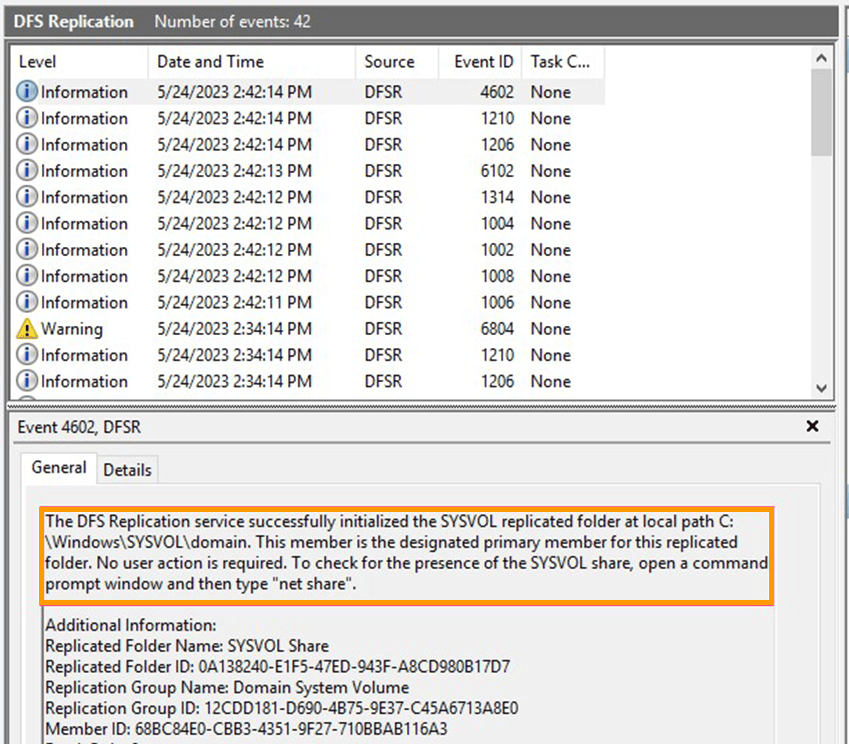
- Examine the DFS Replication event logs for Event ID 4602, which indicates that SYSVOL replication has begun. To ensure the health of your recovered domain controller, study the other logs and do further tests. Figure 4 displays a snapshot of my repaired domain controller’s DFS logs. See AD Forest Recovery – Verify Replication for additional details.
Cleanup Stack
Go to the AWS CloudFormation console to remove the resources produced by the AWS CloudFormation template. Select the stack you made, then click Delete.
Conclusion
As we conclude, it is clear that protecting your Active Directory (AD) infrastructure is more important than ever in the face of escalating ransomware attacks. This article has led you through the steps to putting in place a solid Disaster Recovery (DR) plan utilizing AWS, assuring the resilience of your self-managed AD infrastructure. IT Company also offers AWS Managed Cloud Hosting and automation scripts to make it simple to run routine AD exercises without affecting production processes, increasing your preparedness for any unanticipated difficulties.
While these insights are crucial for bolstering your AD infrastructure, don’t overlook the extraordinary benefits of AWS Managed Cloud Hosting. You get a competitive advantage in the cloud hosting environment by using our AWS Managed Cloud Hosting. This completely managed solution ensures that your company benefits from high availability, scalability, and top-tier security without the hassle of day-to-day maintenance.
AWS Managed Cloud Hosting enables you to concentrate on what is actually important: your core business objectives. It’s a strategic decision that improves operational efficiency, freeing up resources and attention for innovation, growth, and greater client experiences.
Integrating AWS Managed Cloud Hosting into your Company is a step toward future-proofing your organization. Make the wise decision to embrace this service and expand your cloud hosting options. Your company’s future deserves nothing less than the finest, and AWS Managed Cloud Hosting delivers. Secure your company’s digital future today with AWS Managed Cloud Hosting’s unrivaled capabilities.